DDoS Attacks
 On October 21st, a massive Cyber-Attack impacted major websites such as Airbnb, Etsy, Netflix, Reddit, Spotify and Twitter. The nature of the attack is part of a growing trend of Dedicated Denial of Service (DDoS) attacks that utilize infected Internet of Things (IoT) devices. Examples of IoT devices are security cameras and DVRs. For more information on DDoS attacks and IoT, see two recent DCT articles,
On October 21st, a massive Cyber-Attack impacted major websites such as Airbnb, Etsy, Netflix, Reddit, Spotify and Twitter. The nature of the attack is part of a growing trend of Dedicated Denial of Service (DDoS) attacks that utilize infected Internet of Things (IoT) devices. Examples of IoT devices are security cameras and DVRs. For more information on DDoS attacks and IoT, see two recent DCT articles,
IoT Insecurity – The Biggest Consumer Threat Ever? and The Internet is Officially Dead.
Since the Mirai BotNet was made open source (meaning anyone can use it) earlier this year, there has been an increase in Cyber-Attacks using IoT devices. The October 21st DDoS attack force included 50,000 to 100,000 IoT devices.
What makes a device or ‘thing’ vulnerable? The easiest way for a device to be compromised is if it is still using the default User ID and Password. If your router is still using ‘Admin/Admin’ for its ‘User ID/Password’, change it now!
Are You Compromised?
What if you have a device that is compromised? Anecdotally, if you reset the device, it should remove any malware. All the same, I’d also change its User ID (if possible) and Password.
So how can you tell if you have an infected ‘thing’? BullGuard has a tool called IoT Scanner. If you are unfamiliar with BullGuard (as I was), BullGuard is a top-rated European consumer security company and is a pioneer in the IoT and connected device security for consumers. Its scanning tool uses a vulnerability scanning service, Shodan, to identify whether one of the devices on your network is a known vulnerability. Shodan is a search engine for the Internet of Things. It identifies devices that are publicly accessible on the Internet, making them vulnerable to hackers.
Let’s Find Out
It only takes a few steps to find out if any of your devices have been compromised:
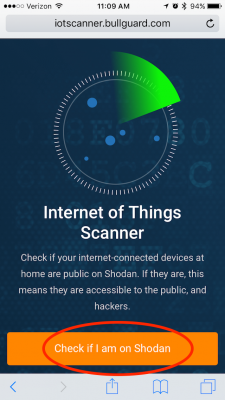
STEP 1: While on your home network, go to BullGuard’s IoT Scanner.
STEP 2: Select ‘Check if I am on Shodan’.
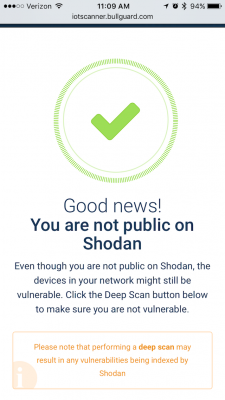
After the scan is complete, hopefully, you will see this:
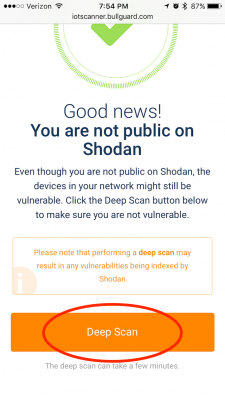
STEP 3: You can choose to do a ‘Deep Scan’ to make sure that all of your devices are not vulnerable. While there is a caution that this may result in vulnerable devices being indexed by Shodan, in my opinion, I’d rather know now than find out after the fact if a device is eventually compromised. So, if you’re game, scroll down a bit and select ‘Deep Scan’.
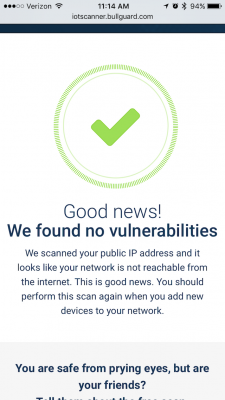
STEP 4: Hopefully, you have no vulnerable devices and will see this:
So, in a few simple steps, you can find out if you’ve been compromised or have the potential for that to occur.
—

Actually, the first D in DDoS is an abbreviation for “Distributed,” not “Dedicated.”
To Tom R. I’m not sure which is the correct word, as doing a search, I stumbled onto both uses. Here is just one example (below), Mindblower!
FFIEC Joint Statement on Dedicated Denial of Service (DDoS …
http://www.ffiec.gov/press/PDF/FFIEC DDoS Joint Statement.pdf · PDF file
distributed denial-of-service (DDoS) attacks on public websites.